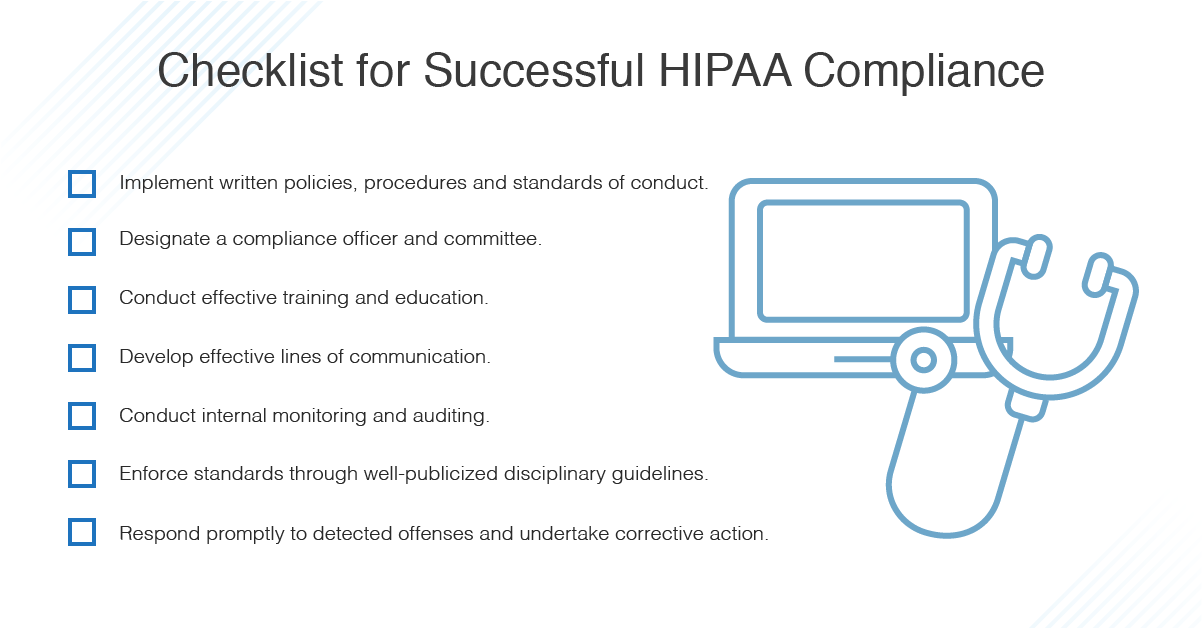
HITECH requires the HHS to periodically monitor all covered entities and select business associates. Microsoft enables customers in their compliance with HIPAA and the HITECH Act and adheres to the HIPAA Security Rule requirements in its capacity as a business associate.
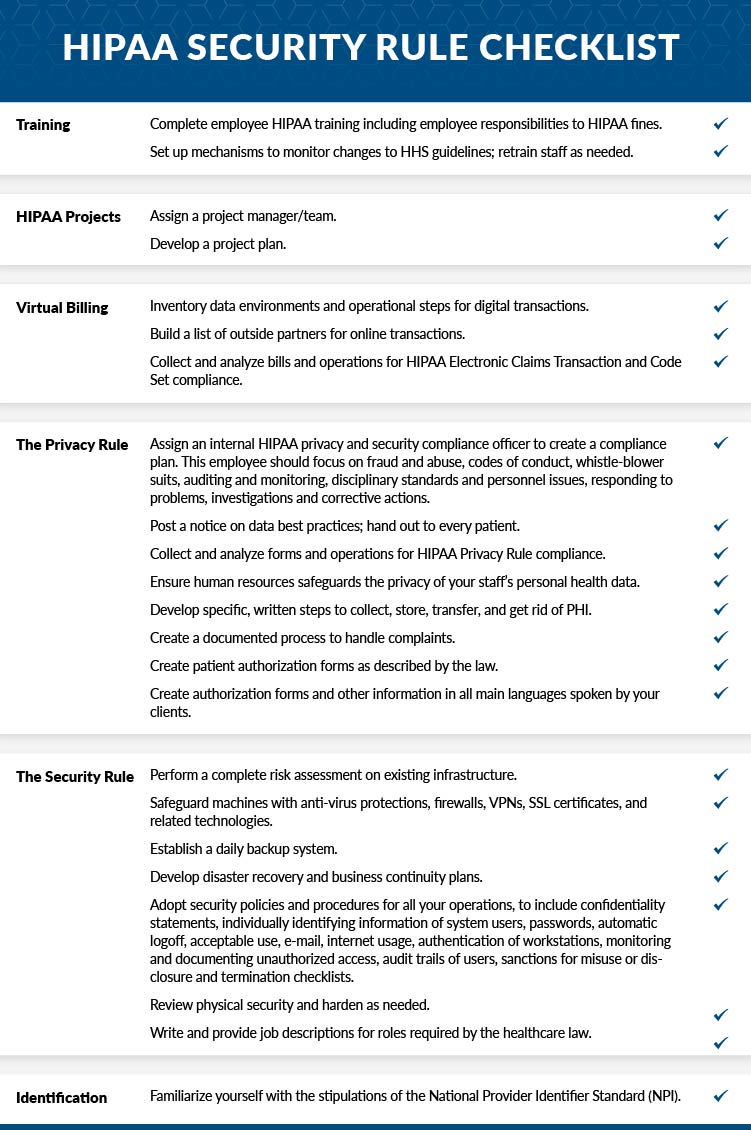 Hipaa Security Rule Checklist What Is The Hipaa Security Rule
Hipaa Security Rule Checklist What Is The Hipaa Security Rule
HITECH AND HIPAA SECURITY STANDARDS AND REGULATIONS The Health Insurance Portability and Accountability Act HIPAA was enacted to protect patient privacy.

Hitech and hipaa security standards and regulations. Assess your current system and determine if it actually protects patient health information. Many CEs and BAs fail in this area because tape- or disk-based backups are moved around freely unencrypted. The first phase audits were launched as a pilot from 2011 to 2012 on 115 identified stakeholders.
Overview of the HITECH Security Standards Rule. Subtitle D of HITECH addressed certain issues relating to the digital storage and transmission of medical records and made changes that allowed the enforcement of compliance with HIPAA Rules. It protects EHR or electronic health records from breaches or improper usage.
Considerations in HIPAAHITECH compliance. HITECH and HIPAA Security Standards and Regulations Patient privacy and from WGU C155 at Western Governors University. Data storage integrity data backup and recovery 3.
It introduced several new security standards and upgraded existing ones to protect all healthcare stakeholders. Electronic PHI has been encrypted as specified in the HIPAA Security Rule by the use of an algorithmic process to transform data into a form in which there is a low probability of assigning meaning without use of a confidential process or key 45 CFR 164304 definition of encryption and such confidential process or key that might enable decryption has not been breached. The link below is to the HIPAA Security Information Series which is a group of educational papers which are designed to give HIPAA covered entities insight into the HIPAA Security Rule and assistance with implementation of the security standards to safeguard electronic protected health information.
HITECH has also strengthened the HIPAA breach notification rule. Both Acts address the security of electronic Protected Health Information ePHI and measures within HITECH support the effective enforcement of HIPAA most notably the Breach Notification Rule and the HIPAA Enforcement Rule. These audits are used to investigate and determine whether providers meet minimum specified standards and are therefore in compliance with the HIPAAs Privacy Rule and Security Rule.
HITECH says to encrypt or destroy data at rest to secure it Section 13402h of Title XIII HITECH Act. Stringent security standards must be developed if theyre not currently in place and applied across the entire organization. Explain how a system will protect patient privacy.
Business associates The HIPAA privacy and security rules and penalties now apply directly to business associates such as banks claims clearinghouses billing firms health information exchanges and software companies as though they were healthcare organizations. Its goal is improving portability and continuity of health insurance coverage and to decrease waste fraud and health insurance abuse. Business associates will now have increased responsibility in safeguarding Protected Health Information PHI and disclosing instances where PHI has been accessed or shared.
The final element of HITECH-specific compliance requirements involves the process of HIPAA and HITECH auditing. Azure Blueprints is a service that helps customers deploy and update cloud environments in a repeatable manner using composable artifacts such as Azure Resource Manager templates to provision. HIPAA and HITECH Audit Requirements.
HITECH requires providers to go through HIPAA certification under the standards of the Omnibus Rule. Revisions to HIPAA and the HITECH Act take the rules of both into consideration. Explain how a system will meet HITECH and HIPAA security standards and regulations including the following.
HITECH was drafted and integrated into the HIPAA framework to extend its protections for PHI into the realm of electronic PHI ePHI. HITECH compliance requirements are similar to those outlined in HIPAA. This interim final rule does not make amendments with respect to those enforcement provisions of the HITECH Act that are not yet effective under the applicable statutory provisions.
The HITECH Act also set the stage for stricter enforcement of the Privacy and Security Rules of HIPAA by mandating security audits of all healthcare providers. HIPAA Security Rule says that data being transmitted must be encrypted CFR 164312e1B. However there is a difference between HIPAA and HITECH.
The HITECH Act required the Secretary of the HHS to ensure guidance was issued annually to covered entities and business associates to help them implement appropriate technical safeguards to ensure the confidentiality integrity and availability of PHI. HITECH generally requires business associates to comply with HIPAA Privacy and Security Rules in the same manner as other covered entities eg health plans. The government never makes it easy.
As mentioned above HITECH compliance rules have strengthened HIPAA violation penalties and stage 3 is likely to further strengthen security and risk assessment requirements already imposed by HIPAA. This interim final rule conforms HIPAAs enforcement regulations to these statutory revisions that are currently effective under section 13410d of the HITECH Act. The purpose of HITECH is to expand the regulations of HIPAA or the Health Information Portability and Accountability Act.
The HITECH Act also strengthened the HIPAA Privacy and Security Rules with respect to electronic health and medical records. The HITECH Act took the HIPAA Privacy and Security Rules into consideration. The Health Insurance Portability and Accountability Act HIPAA and the Health Information Technology for Economic and Clinical Health HITECH Act directly impact health care providers health plans and health care clearinghouses covered entities as they provide the legal framework for enforceable privacy security and breach notification rules related to protected health information PHI.
Following is a summary of the major data security components of the HITECH Act. Below well cover everything you need to know about HITECHs security standards.